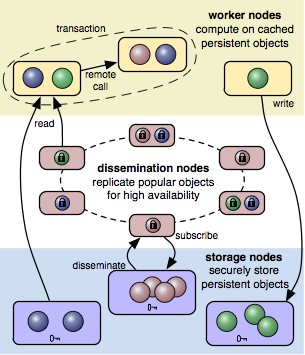
Fabric is a high-level programming language for building open distributed applications with strong security. Fabric enables securely computing and storing information, and sharing code and data across trust boundaries. It is being developed by the Applied Programming Languages Group at Cornell University.
Fabric presents a single-system image of all resources that can be named by it, making programming easy. It is a decentralized system with no central security enforcement mechanism, yet it provides security guarantees to mutually distrusting users. The key to strong, compositional information security guarantees is the use of information flow control.
Fabric's programming language, based on Jif, controls the placement of computation and data through type annotations that set policies for information security. Using information flow control, Fabric also makes mobile code secure. Strong consistency is ensured through a hierarchical two-phase commit protocol that respects information security. Fabric also leverages peer-to-peer replication to provide high availability.
Mailing list
Sign up for news about Fabric!
Send mail to fabric-users-l-request@cornell.edu with a subject line of join. Or turn on JavaScript to see the sign-up form.
Releases
In addition to the downloads below, the full history of Fabric releases is also available on GitHub:
Current release
Fabric 0.3.0 (June 2016) includes support for object partitioning and has several bug fixes. See the ChangeLog for details.
Previous releases and branches
There is a branch of 0.2.2 that incorporates support for state warranties, as described in our NSDI 2014 paper.
| Version | Release date | ||
|---|---|---|---|
| July 2014 | Reference manual | ChangeLog | |
| July 2014 | Reference manual | ChangeLog | |
| June 2013 | Reference manual | ChangeLog | |
| October 2012 | Reference manual | ChangeLog | |
| September 2010 |
Related group publications
-
Reduced communication for distributed transactions through time-dependent guarantees
Ph.D. dissertation, Cornell University, August 2019. Tom Magrino. [ @phdthesis{magrino-dissertation, title="Reduced communication for distributed transactions through time-dependent guarantees", author="Tom Magrino", url="https://tommagrino.com/papers/dissertation.pdf", month="August", year="2019"} ] -
Efficient, consistent distributed computation with predictive treaties
Low-coordination enforcement of semantic consistency using time-dependent predicates
ACM SIGOPS/EuroSys European Conference on Computer Systems, March 2019. Tom Magrino, Jed Liu, Nate Foster, Johannes Gehrke, and Andrew C. Myers. [ @inproceedings{ptreaties, title="Efficient, consistent distributed computation with predictive treaties", author="Tom Magrino and Jed Liu and Nate Foster and Johannes Gehrke and Andrew C. Myers", booktitle="ACM SIGOPS/EuroSys European Conference on Computer Systems", url="http://www.cs.cornell.edu/andru/papers/ptreaties", month="March", year="2019"} ] -
Fabric: Building open distributed systems securely by construction
A secure, decentralized, distributed programming system based on information flow control
J. Computer Security, 25(4–5):319–321, May 2017. Jed Liu, Owen Arden, Michael D. George, and Andrew C. Myers. [ @article{jfabric, title="Fabric: Building open distributed systems securely by construction", author="Jed Liu and Owen Arden and Michael D. George and Andrew C. Myers", volume="25", number="4–5", url="http://www.cs.cornell.edu/andru/papers/jfabric", pages="319–321", month="May", year="2017"} ] -
Safe serializable secure scheduling: transactions and the trade-off between security and consistency
A side channel created by an intrinsic conflict between consistency and security, and a fix
23rd ACM Conf. on Computer and Communications Security (CCS), pp. 229–241, October 2016. Isaac Sheff, Tom Magrino, Jed Liu, Andrew C. Myers, and Robbert Van Renesse. [ @inproceedings{abrtchan, title="Safe serializable secure scheduling: transactions and the trade-off between security and consistency", author="Isaac Sheff and Tom Magrino and Jed Liu and Andrew C. Myers and Robbert Van Renesse", booktitle="23rd ACM Conf. on Computer and Communications Security (CCS)", url="http://www.cs.cornell.edu/andru/papers/abrtchan", pages="229–241", month="October", year="2016"} ] -
A calculus for flow-limited authorization
A language that uses information flow to check the code of authorization mechanisms.
29th IEEE Computer Security Foundations Symp. (CSF), pp. 135–147, June 2016. Owen Arden and Andrew C. Myers. [ @inproceedings{flac, title="A calculus for flow-limited authorization", author="Owen Arden and Andrew C. Myers", booktitle="29th IEEE Computer Security Foundations Symp. (CSF)", url="http://www.cs.cornell.edu/andru/papers/flac", pages="135–147", month="June", year="2016"} | TR ] -
Flow-limited authorization
Ph.D. dissertation, Cornell University, 2016. Owen Arden. [ @phdthesis{owen-thesis, title="Flow-limited authorization", author="Owen Arden", url="http://www.cs.cornell.edu/andru/papers/FLA_OwenArden.pdf", year="2016"} ] -
Building distributed systems with information flow control
Ph.D. dissertation, Cornell University Department of Computer Science, August 2015. K. Vikram. [ @phdthesis{vikram-thesis, title="Building distributed systems with information flow control", author="K. Vikram", url="http://www.cs.cornell.edu/andru/papers/kv-thesis.pdf", month="August", year="2015"} ] -
Flow-limited authorization
An expressive logic for reasoning about the interaction between authorization and information flow.
28th IEEE Computer Security Foundations Symp. (CSF), pp. 569–583, July 2015. Owen Arden, Jed Liu, and Andrew C. Myers. [ @inproceedings{flam, title="Flow-limited authorization", author="Owen Arden and Jed Liu and Andrew C. Myers", booktitle="28th IEEE Computer Security Foundations Symp. (CSF)", url="http://www.cs.cornell.edu/andru/papers/flam", pages="569–583", month="July", year="2015"} | TR | slides ] -
A calculus for flow-limited authorization: technical report
Technical report 1813–42406, Cornell University Computing and Information Science, February 2015. Owen Arden and Andrew C. Myers. [ @techreport{flac-tr, title="A calculus for flow-limited authorization: technical report", author="Owen Arden and Andrew C. Myers", institution="Cornell University Computing and Information Science", number="1813–42406", url="http://hdl.handle.net/1813/42406", month="February", year="2015"} ] -
A language-based approach to secure quorum replication
Quorum replication with information flow control can simultaneously enforce all three core security properties: confidentiality, integrity, and availability.
9th ACM SIGPLAN Workshop on Programming Languages and Analysis for Security (PLAS), August 2014. Lantian Zheng and Andrew C. Myers. [ @inproceedings{zm14-plas, title="A language-based approach to secure quorum replication", author="Lantian Zheng and Andrew C. Myers", booktitle="9th ACM SIGPLAN Workshop on Programming Languages and Analysis for Security (PLAS)", url="http://www.cs.cornell.edu/andru/papers/plas14", month="August", year="2014"} ] -
Defining and enforcing referential security
New security properties related to referential integrity and persistence can be soundly enforced by a type system.
3rd Conf. on Principles of Security and Trust (POST), pp. 199–219, April 2014. Jed Liu and Andrew C. Myers. [ @inproceedings{persist, title="Defining and enforcing referential security", author="Liu, Jed and Myers, Andrew C.", booktitle="3rd Conf. on Principles of Security and Trust (POST)", url="http://www.cs.cornell.edu/andru/papers/persist", pages="199–219", month="April", year="2014"} | TR ] -
Warranties for faster strong consistency
Distributed transactions can be sped up by giving clients time-limited invariants on state and computation.
11th USENIX Symp. on Networked Systems Design and Implementation (NSDI), pp. 513–517, April 2014. Jed Liu, Tom Magrino, Owen Arden, Michael D. George, and Andrew C. Myers. [ @inproceedings{warranties, title="Warranties for faster strong consistency", author="Jed Liu and Tom Magrino and Owen Arden and Michael D. George and Andrew C. Myers", booktitle="11th USENIX Symp. on Networked Systems Design and Implementation (NSDI)", url="http://www.cs.cornell.edu/andru/papers/warranties", pages="513–517", month="April", year="2014"} ] -
Towards a secure federated information system
Ph.D. dissertation, Cornell University Department of Computer Science, August 2012. Jed Liu. [ @phdthesis{liu-thesis, title="Towards a secure federated information system", author="Jed Liu", url="http://www.cs.cornell.edu/andru/papers/jed-liu-dissertation.pdf", month="August", year="2012"} ] -
Sharing mobile code securely with information flow control
IEEE Symp. on Security and Privacy, pp. 191–205, May 2012. Owen Arden, Michael D. George, Jed Liu, K. Vikram, Aslan Askarov, and Andrew C. Myers. [ @inproceedings{oakland12, title="Sharing mobile code securely with information flow control", author="Owen Arden and Michael D. George and Jed Liu and K. Vikram and Aslan Askarov and Andrew C. Myers", booktitle="IEEE Symp. on Security and Privacy", url="http://www.cs.cornell.edu/andru/papers/mobile.html", pages="191–205", month="May", year="2012"} ] -
Predictive mitigation of timing channels in interactive systems
18th ACM Conf. on Computer and Communications Security (CCS), pp. 563–574, October 2011. Danfeng Zhang, Aslan Askarov, and Andrew C. Myers. [ @inproceedings{zam11, title="Predictive mitigation of timing channels in interactive systems", author="Danfeng Zhang and Aslan Askarov and Andrew C. Myers", booktitle="18th ACM Conf. on Computer and Communications Security (CCS)", url="http://www.cs.cornell.edu/andru/papers/gentiming.html", pages="563–574", month="October", year="2011"} ] -
Attacker control and impact for confidentiality and integrity
Logical Methods in Computer Science, 7(3), September 2011. Aslan Askarov and Andrew C. Myers. [ @article{am11, title="Attacker control and impact for confidentiality and integrity", author="Aslan Askarov and Andrew C. Myers", volume="7", number="3", url="http://www.cs.cornell.edu/andru/papers/robknowledge-lmcs.pdf", month="September", year="2011"} ] -
Predictive black-box mitigation of timing channels
17th ACM Conf. on Computer and Communications Security (CCS), pp. 297–307, October 2010. Aslan Askarov, Danfeng Zhang, and Andrew C. Myers. [ @inproceedings{azm10, title="Predictive black-box mitigation of timing channels", author="Aslan Askarov and Danfeng Zhang and Andrew C. Myers", booktitle="17th ACM Conf. on Computer and Communications Security (CCS)", url="http://www.cs.cornell.edu/andru/papers/timing.html", pages="297–307", month="October", year="2010"} ] -
A semantic framework for declassification and endorsement
19th European Symposium on Programming, pp. 64–84, March 2010. Aslan Askarov and Andrew C. Myers. [ @inproceedings{am10, title="A semantic framework for declassification and endorsement", author="Aslan Askarov and Andrew C. Myers", booktitle="19th European Symposium on Programming", url="http://www.cs.cornell.edu/andru/papers/robknowledge.pdf", pages="64–84", month="March", year="2010"} ] -
Fabric: a platform for secure distributed computation and storage
22nd ACM Symp. on Operating System Principles (SOSP), pp. 321–334, October 2009. Jed Liu, Michael D. George, K. Vikram, Xin Qi, Lucas Waye, and Andrew C. Myers. [ @inproceedings{fabric09, title="Fabric: a platform for secure distributed computation and storage", author="Jed Liu and Michael D. George and K. Vikram and Xin Qi and Lucas Waye and Andrew C. Myers", booktitle="22nd ACM Symp. on Operating System Principles (SOSP)", url="http://www.cs.cornell.edu/andru/papers/fabric-sosp09.html", pages="321–334", month="October", year="2009"} ]
